Using Azure Sentinel for insights in Workplace Occupancy
Azure Sentinel provides a great overview of security events in your organization. You can collect security events at a large scale. Now there are quite a few blogs about all the things you can do with it and I am by no means an expert. However, since we are all going back to the office, we had an interesting use case. Like most companies we have build a nice app to book a spot at the Office and we have been able to accommodate most people in working from the office when it makes sense.
Yet sometimes you want to have some reporting capabilities as well. Instead scanning presence based on GPS or Tags or extending the App to phone home and tell us where people where we ended up looking at Azure Sentinel.
You can log all Office 365 Audit data to Azure Sentinel with the O365 Log connector. The cool thing about that is that it is ‘free’ if you want to capture only the last seven days of information. Now in our case we wanted to make sure that there were not too many people at one of our office locations. Seven days is sufficient for that case, and there is no need to buy additional resources.
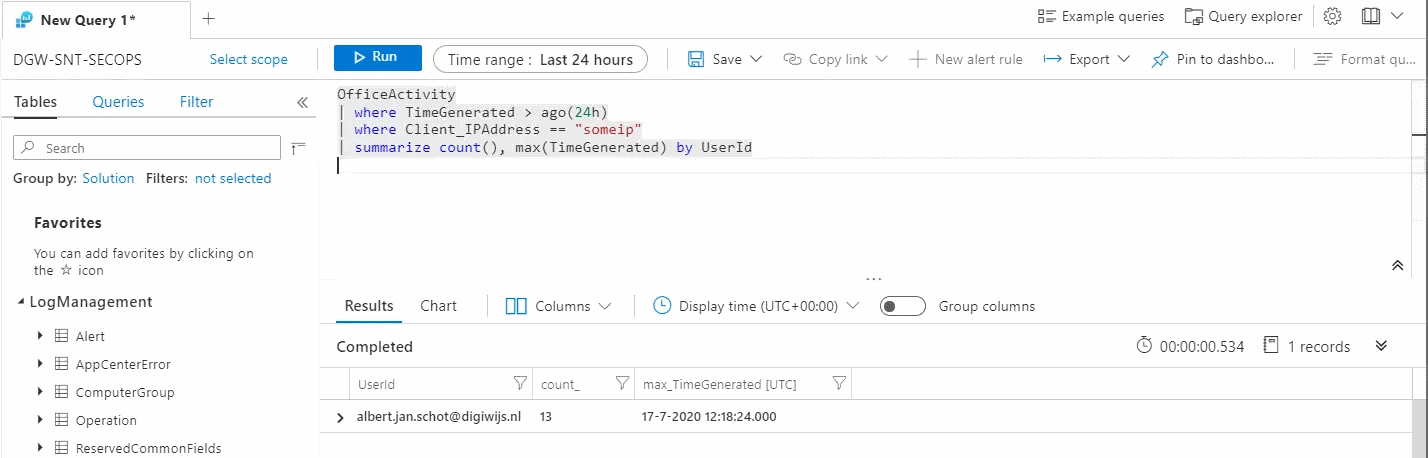
Once you have the Unified Audit Log enabled and have setup a Log Analtyics workspace you can play around with the data you have. Keep in mind that the data is not ‘real time’ and there is a slight delay before data shows up in your logs. With the O365 log connector configured all O365 data ends up in the OfficeActivity bucket. You can query this bucket and get some additional data. In our case we needed a query that returns all entries from a specific office location (based on IP address) and only within a specific timeframe.
OfficeActivity
| where TimeGenerated > ago(24h)
| where Client_IPAddress == "OfficeIP"
Once you have that data you can group by the User Identifier (UserId), or UserKey if you do not want the UPN to be visible. By grouping and summarizing the data you get an overview of when a user has logged in during that 24h timeframe.
OfficeActivity
| where TimeGenerated > ago(24h)
| where Client_IPAddress == "OfficeIP"
| summarize count(), max(TimeGenerated) by UserId
Resulting in a nice report with all your users that have logged in during the last 24 hours.
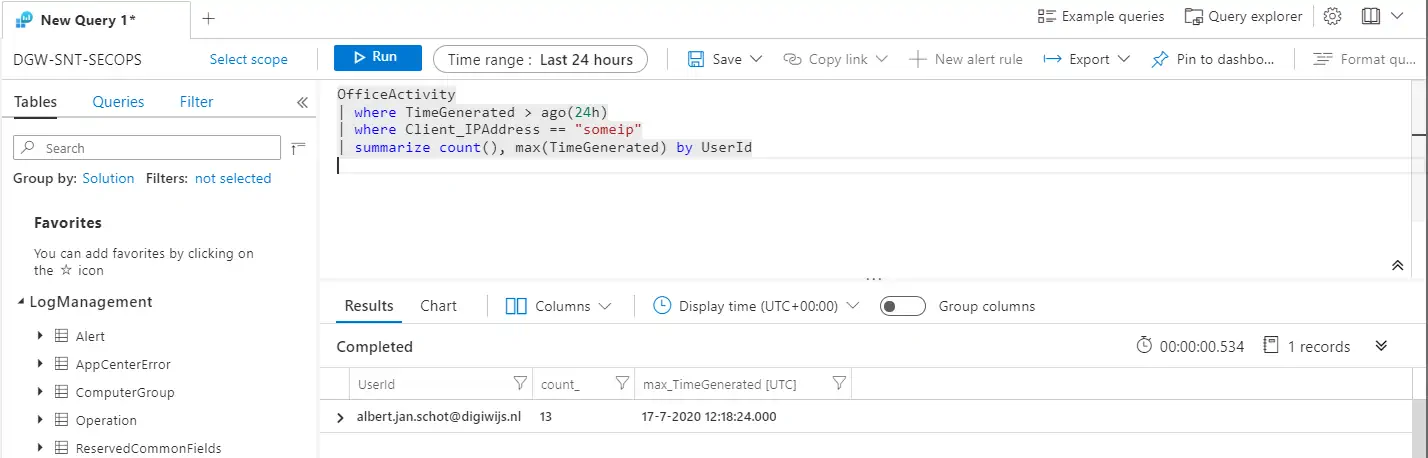
If you are not comfortable with the UPN showing up you can use the UserKey as that does not show identifiable information directly in the report.
Once you have this report in place you can also add alert rules. An alert rule could be to send an e-mail to your HR department if there are to many people on your office location. Or you can ‘disable’ the registration app and prevent new people to book a slot. Sending e-mails is the default option and just would serve as a notification. But as with all alert rules you can also add your own Logic App or Function to trigger custom events. Using a Logic App or Function you could even disable tags so people cannot open the front door.
Given the fact that Sentinel might not be build for this, it still was a fun way to play around with data already present and make our Office a bit safer all while learning about new stuff!